I’m playing with the grsecurity patches for Linux. Unfortunately 2.6.8 changed in a way that causes major headache for the grsec team, so no planned release date for a new patch. Having some problems with strange enforcements of rlimits, potentially linked to the rlimit auditing code. I’ll hopefully get time to tinker with SELinux too.
Category: Tech
NTL hell, Amazon + Pixmania idiots
NTL phone message tells customers to fuck off. “We don’t give a f..k about you… we just will f..k you”. I’m just pleased they are being honest for once.
I managed to re-apply for an Amazon account with the same e-mail address and gained access to my previous purchases history and credit card history. I’ve e-mailed a number of time but Amazon just don’t care. I actually want to make a book purchase but cannot (as I now have two accounts with the same e-mail address (i.e: username) and it gets confused). I’m just going to purchase them elsewhere.
(more…)
2.6.7-8 default window scaling settings
My new Fedora installation was playing up with certain web sites resulting in *very* slow download (I could see the words drawing on my screen one by one). A ethereal dump showed a nice big window size, but max 120 byte packets and an ack for each one!
Well it turns out since about kernel 2.6.7, the default tcp_window_scale setting has been 7. The problem is, as was with ECN, there are lots of broken routers out there which break window scaling (they strip the TCP options, which is totally against RFC, and common sense). So the other end doesn’t know you’re scaling, so it’ll think you set (or you think it set) a tiny ikle window size.
Anyway I fixed it for now with a ‘net.ipv4.tcp_default_win_scale = 0’ in my /etc/sysctl.conf, but there is a new kernel patch floating around which seems to be a bit cleverer and will be due in the next kernel.
FreeS/WAN Sonicwall example
Here’s a (possibly) handy little set of configs and such to help you get
the FreeS/WAN IPSEC implementation working with a Sonicwall firewall in tunnel mode. It should work in transport mode with minimal changes but I have not tested that myself.
This is a working config with the sensitive information obsucated (mostly the external IPs of the firewalls and the secret key).
“fre.esw.an.ip” = freeswan gateway ip and
“son.icw.all.ip” = sonicwall gateway ip.
I’ve found other examples which state you need the “SonicWall Unique Identifier” but I found this to be unnecessary (in fact I couldn’t get it working correctly using any leftid= combinations)
Diagram
Left Network
10.0.0.0/8
|
--------------------
| FreeSwan GW |
| fre.esw.an.ip |
--------------------
|
The InterNET(tm)
|
--------------------
| SonicWall GW |
| son.icw.all.ip |
--------------------
|
Right Network
192.168.1.0/24
ipsec.conf
config setup
interfaces=%defaultroute
klipsdebug=none
plutodebug=none
plutoload=%search
plutostart=%search
plutowait=no
uniqueids=yes
conn fswn-swll
# PFS doesn't work so turn it off
pfs=no
keyingtries=0
ikelifetime=28800
keylife=5h
disablearrivalcheck=no
# Freeswan Side
left=fre.esw.an.ip
leftsubnet=10.0.0.0/8
leftnexthop=%defaultroute
# Sonicwall Side
right=son.icw.all.ip
rightsubnet=192.168.1.0/24
authby=secret
# you'll need to do "ipsec auto --up fswn-swll" to start this up
# unless you use auto=start, but thats just basic freeswan stuff
auto=add
ipsec.secrets
fre.esw.an.ip son.icw.all.ip : PSK "allthefish"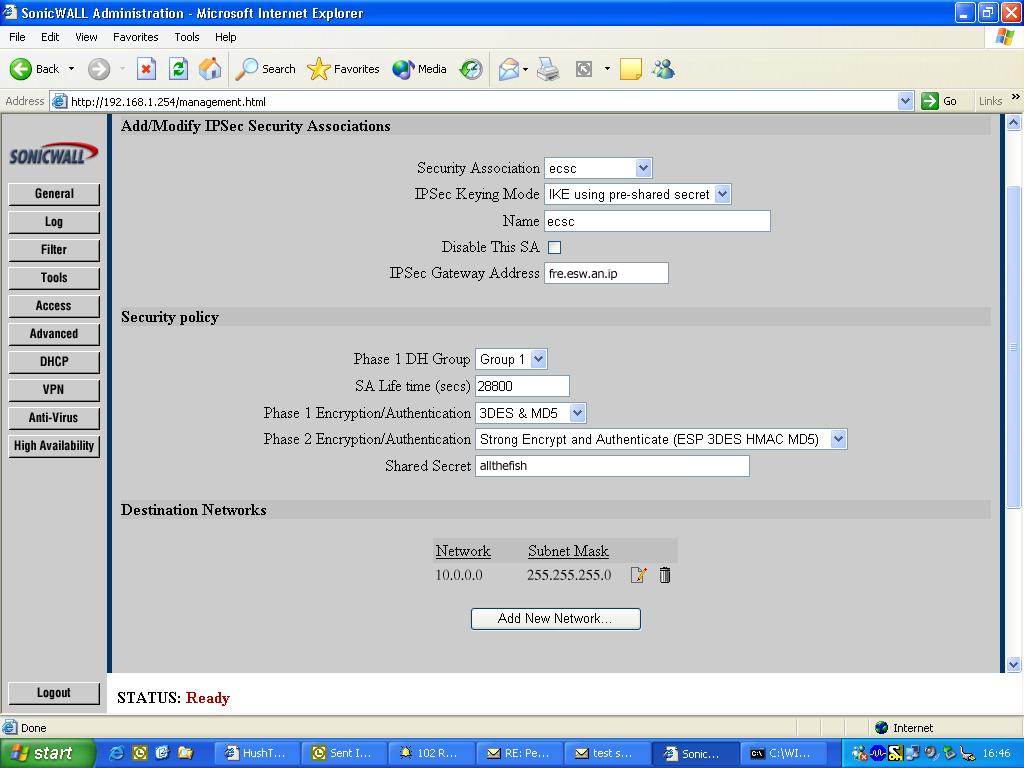
gnome kismet client
I’m working on a gnome kismet client. It’s written in python, check out the screen shot.
yum/up2date suck, new job
I’ve come to the realisation that yum and up2date completely and utter suck. Why is it yum has spent the last 20mins downloading rpm headers from the dag repository? Why is it up2date can’t search properly? why does yum return search results in an unreadable way? why do both of them, at the mere hint of something going wrong, spurt out a big python backtrace that is very little use to very many people. Why are these tools SO BAD? How difficult IS THE PROBLEM? Debian have got it right with apt. Headers are downloaded in 30 seconds, search supports regular expressions! There is even an RPM ENABLED version of apt. Why wasn’t this used in Fedora? Why up2date with it’s crappy secretive SSL and XML and SOAP and crapness.
I can only imagine it’s due to RedHat wanting the world to develop their Enterprise updatering system for free. Well I’m not contributing until I at least see that either a) I’m doing something wrong and it can all be fixed with an option. or b) someone can explain the good reason why these tools exist.
Also, I have a new job. It’s lots of fun. I’m responsible for the security of some 30 million UK NHS patient records.
RHCE, dsbackup, qemu, nfs, firestorm, m4
I passed my RHCE exam last month.
I’ve released v0.1 of dsbackup, an rsync based backup system.
I’m totally impressed with qemu the Intel and PPC cpu emulator. It’s far faster than bochs and I’ve not had any of the problems that I used to with Bochs (Fedora wouldn’t even get to the installer screen). Apparently the code is far cleaner and better thought out, which is allowing Gianni to do some rather clever things regarding hardward reverse engineering.
I’ve been implementing some NFS services at work over the last few months. I have to say it’s not as bad as I thought it would be. Don’t get me wrong, it’s quite horrifically messy from a security point of view (firewalling rpc, eesh) but not as insanely lame as I had first imagined.
I also begun work on a port scan detector for Firestorm but thats on hold at the moment whilst we discuss some implementation details of the tcp connection tracker. I’m now adding support for disk saving in between restarts for macwatch.
I’ve also learnt the M4 macro language. Cute. And handy.
RedHat, Firestorm, 802.11b and rpm2html
I’ve been working on my qmail rpms for RedHat ES/AS/Fedora. I’ve even started some documentation. It’s all on my RedHat page.
I’ve also been working on Firestorm, improving the arp decoder and developing my macwatch arpwatch clone. Hopefully this will appear in the latest Firestorm tree soon.
I recently ditched my aging Linux wireless bridge/router/firewall in favour of a little Linksys device that cost no more than 60 pounds, uses considerably less electricity and makes almost no noise. The price is impressive and even the device seems to work ok. One thing it can’t deal with properly at all is the TCP ECN flag. The web admin port just sends a RST. Can you believe a Cisco company would make this mistake? Yes. I can.
Also, I’ve created an rpm2html index of all the RPMs in my downloads tree. Some are old crap I’ve not bothered deleting yet, but there is some stuff in there that will be useful to someone (not just google).
Gianni will be home from Luxembourg soon.
Firestorm Debian packages
I’ve built some Firestorm debs for x86 from the latest snapshot (0.5.5-pre3). I had to remove a little bit of verbose debug code from the linux capture driver. available here..
Ethereal ELOG support and keepalived
Updated my Firestorm ELOG alert file support patch for Ethereal (0.10.0). Get it here.
I’ve been playing with keepalived over the last couple of weeks. It’s basically an entire Linux HA cluster system. It does the job of heartbeat for failover and incorporates LVS for load balanced services. It looks really great but I’ve managed to upset it a few times by restarting the daemon too much. Also I’ve found using bonded ethernet interfaces with multicast traffic results in multiple copies of the packets coming out of bond0, which really confuses the keepalived anti-replay sequence numbers (Hey, I’ve seen that packet already!). I’ve reported it to the keepalived guys and will do the same for the bonding people. I’m not sure whose problem it is to solve.
New GPG key
I’ve updated my GPG key. I’ve added a new encryption key as my old one expires in Jan 2004. I also removed an old, irrelevant, signature. Update your keyrings people.
Qmail, RedHat and Firestorm
I’ve built some packages of djbs software (qmail, daemontools, djbdns…) for RedHat ES.
I’ve also been working on Firestorm again, primarily on my mac/arp watcher preprocessor. It now saves state between restarts, and reports on more nefarious ethernet/arp. It’ll be included in the next release of Firestorm.