Here’s a (possibly) handy little set of configs and such to help you get
the FreeS/WAN IPSEC implementation working with a Sonicwall firewall in tunnel mode. It should work in transport mode with minimal changes but I have not tested that myself.
This is a working config with the sensitive information obsucated (mostly the external IPs of the firewalls and the secret key).
“fre.esw.an.ip” = freeswan gateway ip and
“son.icw.all.ip” = sonicwall gateway ip.
I’ve found other examples which state you need the “SonicWall Unique Identifier” but I found this to be unnecessary (in fact I couldn’t get it working correctly using any leftid= combinations)
Diagram
Left Network
10.0.0.0/8
|
--------------------
| FreeSwan GW |
| fre.esw.an.ip |
--------------------
|
The InterNET(tm)
|
--------------------
| SonicWall GW |
| son.icw.all.ip |
--------------------
|
Right Network
192.168.1.0/24
ipsec.conf
config setup
interfaces=%defaultroute
klipsdebug=none
plutodebug=none
plutoload=%search
plutostart=%search
plutowait=no
uniqueids=yes
conn fswn-swll
# PFS doesn't work so turn it off
pfs=no
keyingtries=0
ikelifetime=28800
keylife=5h
disablearrivalcheck=no
# Freeswan Side
left=fre.esw.an.ip
leftsubnet=10.0.0.0/8
leftnexthop=%defaultroute
# Sonicwall Side
right=son.icw.all.ip
rightsubnet=192.168.1.0/24
authby=secret
# you'll need to do "ipsec auto --up fswn-swll" to start this up
# unless you use auto=start, but thats just basic freeswan stuff
auto=add
ipsec.secrets
fre.esw.an.ip son.icw.all.ip : PSK "allthefish"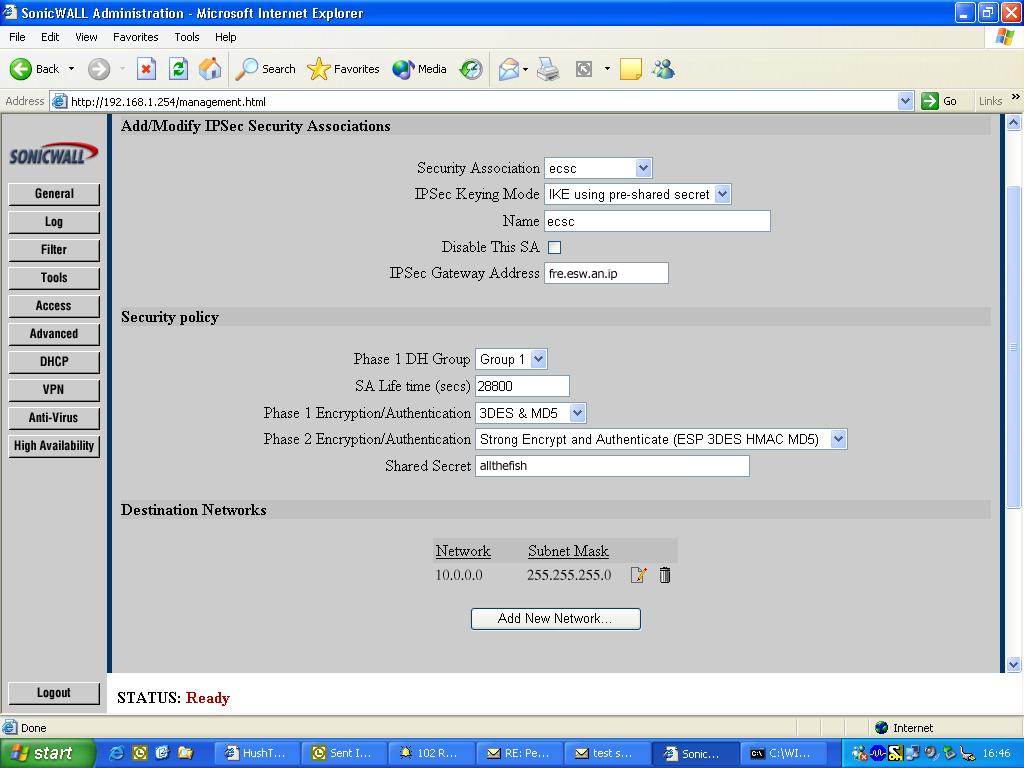
Leave a Reply